Author: Simran Mann, J.D. Candidate at the University of Ottawa
The Women in Technology (WIT) committee celebrated its second annual International Women’s Day event on March 7th at The Loft (18 Tank House Lane, Toronto). The theme of this year’s event was “#InspireInclusion: If Not Her, Then Whom?”, aimed at highlighting the unique challenges and triumphs of women in law and technology.

 Standing up from left to right: (1) Tetyana Klimova, Lawyer at EY Law LLP; and (2) Jennifer Davidson, Board Member of CAN-TECH and Partner at Deeth Williams Wall LLP.
Standing up from left to right: (1) Tetyana Klimova, Lawyer at EY Law LLP; and (2) Jennifer Davidson, Board Member of CAN-TECH and Partner at Deeth Williams Wall LLP.
With a full house event, this evening sparked reflection, compassion, and unity. With women from all walks of life, the room invited insightful dialogue and discussion. The evening kicked off with opening remarks from Jennifer Davidson, followed by Tetyana Klimova who helped moderate this year’s event.
Fireside Chat
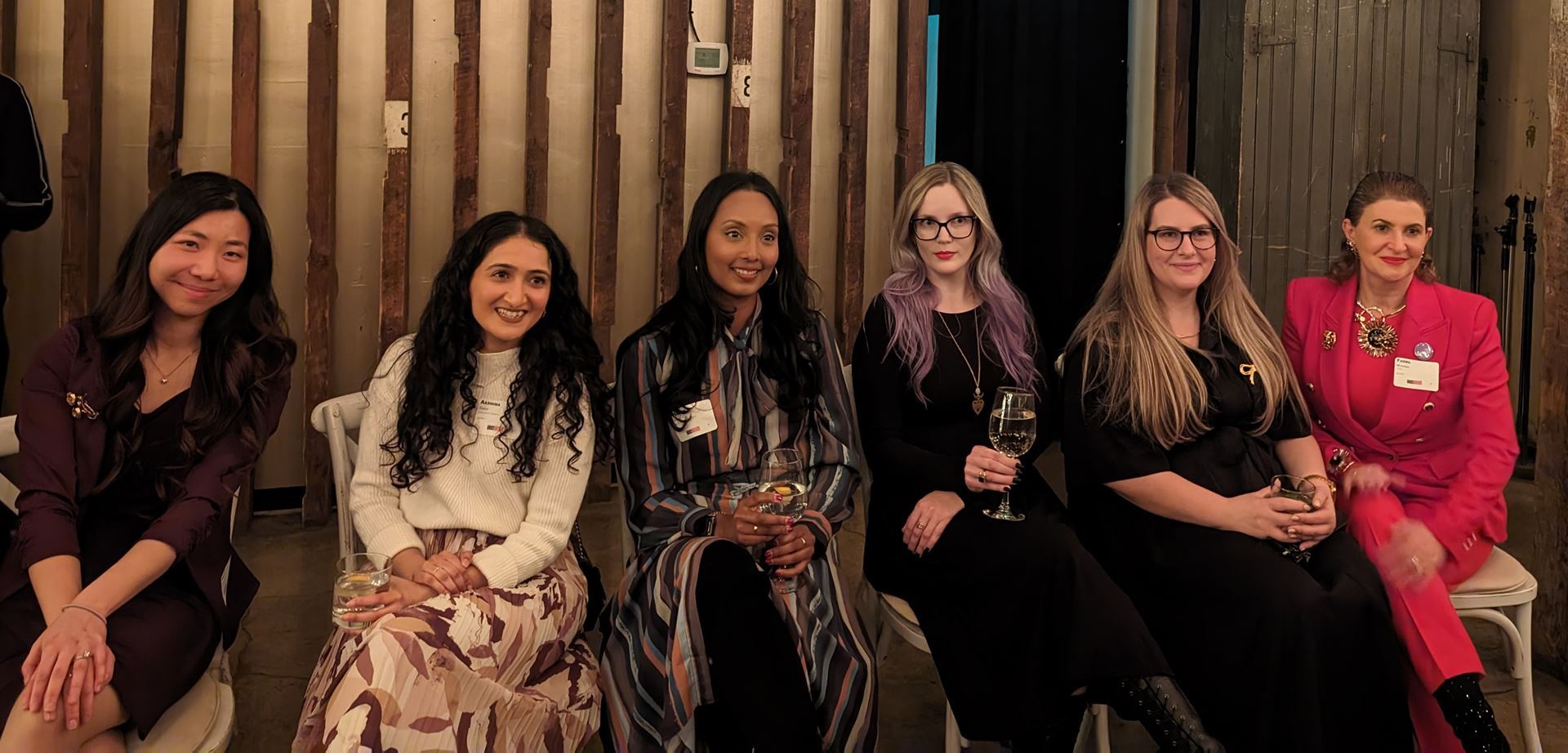 Left to right: (1) Wendes Keung, Co-Chair of WIT and Associate at McCarthy Tétrault LLP; (2) Aashima Singh, Senior Legal Counsel at Lightspeed Commerce; (3) Taslenna Shairulla, Senior Legal Counsel and Chief Privacy Officer at Capital One; (4) Breanna Needham, Associate at DLA Piper; (5) Christine Jackson, Partner at Osler, Hoskin & Harcourt LLP; and (6) Fadwa Mohanna, Co-Founder and CEO at One37.
Left to right: (1) Wendes Keung, Co-Chair of WIT and Associate at McCarthy Tétrault LLP; (2) Aashima Singh, Senior Legal Counsel at Lightspeed Commerce; (3) Taslenna Shairulla, Senior Legal Counsel and Chief Privacy Officer at Capital One; (4) Breanna Needham, Associate at DLA Piper; (5) Christine Jackson, Partner at Osler, Hoskin & Harcourt LLP; and (6) Fadwa Mohanna, Co-Founder and CEO at One37.
Featured above are the six extraordinary women who shared their personal stories about overcoming obstacles and reaching new heights. Wendes Keung reminded the room that while imposter syndrome can manifest as a result of perfectionism and self-doubt, it does not define your true abilities. Aashima Singh emphasized the importance of staying true to yourself, even when it does not succumb to other people’s expectations. Taslenna Shairulla explained how failures can serve as valuable lessons and should not deter anyone from achieving their goals. Breanna Needham emphasized that resiliency is not just breaking the glass ceiling, but understanding when to redirect your efforts when the situation no longer serves you. Christine Jackson helped to reframe the conversation on work-life balance by changing how we view priorities through the glass ball theory. Last but not least, Fadwa Mohanna emphasized the importance of women supporting other women and having strong female role models when navigating the gender disparity in technology. Overall, these six women helped to inform, influence, and inspire the roles that women play in society.
Tech Trivia
.jpg) Featured: Fadwa Mohanna and the vintage brooches.
Featured: Fadwa Mohanna and the vintage brooches.

Following the fireside chat, attendees participated in a game of trivia. Members of the winning team each received a vintage brooch courtesy of Fadwa Mohanna. Inspired by the historical significance of jewelry in the suffragette movement, these brooches symbolize strength and resilience. Inevitably, with the event attracting many talented and smart minds, two teams tied for first place. Thanks to Fadwa, there were plenty of beautiful brooches made available!
Thank You
 Top row from left to right: (1) Taslenna Shairulla; (2) Breanna Needham; (3) Kuljit Bhogal (Co-Chair of WIT and Associate at Osler, Hoskin & Harcourt LLP); (4) Fadwa Mohanna; and (5) Tetyana Klimova. Bottom row from left to right: (1) Aashima Singh; (2) Wendes Keung; and (3) Mallory Allan (Associate Legal Counsel at Healthcare of Ontario Pension Plan).
Top row from left to right: (1) Taslenna Shairulla; (2) Breanna Needham; (3) Kuljit Bhogal (Co-Chair of WIT and Associate at Osler, Hoskin & Harcourt LLP); (4) Fadwa Mohanna; and (5) Tetyana Klimova. Bottom row from left to right: (1) Aashima Singh; (2) Wendes Keung; and (3) Mallory Allan (Associate Legal Counsel at Healthcare of Ontario Pension Plan).
Both Kuljit Bhogal and Wendes Keung played an instrumental role in the curation of this year’s International Women’s Day event. Thank you to this year’s sponsors: Blakes, Cassels & Graydon LLP, Deeth Williams Wall LLP, McCarthy Tétrault LLP, and WeirFoulds LLP. It is thanks to the support of volunteers, sponsors, and attendees that the event was such a success.
From discussions on breaking barriers to celebrating achievements, the event served as a powerful reminder of the progress made and the work still ahead in promoting gender equality and diversity. The WIT committee hopes that this event encourages more people to champion inclusion in their workplaces and communities, embodying the spirit of the mission to #InspireInclusion in their daily lives.